Data-Centric Security: Cyber Survival Kit in the 2020’s

“A comprehensive data security approach ensures the right people, internal or external, always receive access to the appropriate data and information at the right time and place.”1
It is clear the cyber threat surface is large and growing larger. While perimeter security is still a necessary line of cyber defense, it is no longer the last or most important. Three key truths have been acknowledged and with that insight the cyber defense paradigm is at present undergoing a dramatic shift. The first concept is that breaches will occur, accept it and account for it. The second is related to the first, it cannot be assumed that any place in your network is safe and trusted. The third and most powerful of these is that data/information is the true asset which needs to be protected. With these three truths organizations are now rethinking how they prepare for and fight the cyber security war.
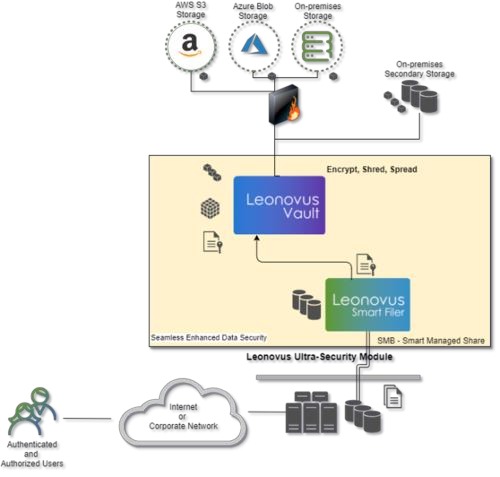
Based on the three truths, the strongest survival kit for cyber security in the 2020’s is a zero-trust strategy with a data- centric security-based system. Leonovus Inc., a secure data management software company, offers just such as solution. The Leonovus solution is built to withstand and accept cyber intrusion. All data is known, protected, and tracked. All interactions are only with recently authenticated and authorized entities, protected by two-factor authentication. Ownership is tightly controlled and managed, even administrators do not have access to data objects unless granted by the owner.
The Leonovus suite of data management tools offer an organization what it needs for a complete end-to-end data-centric solution. This solution easily integrates with the organization’s zero-trust strategy and architecture. Employing its proprietary Encrypt-Shred-Spread technology, it seamlessly integrates with the organization’s existing storage infrastructure and network architecture, working both on-premises and in the cloud, extending the data-centric controls across the entire architecture. And it provides these cybersecurity capabilities for the full lifespan of the data and beyond.
Designed for simplicity and flexibility, the solution does not require changes in how the data is used. Applications, services, and users all interact with the data the same way they always have. The system is designed to ensure the right users get access to the right data, at the right time, but securely.
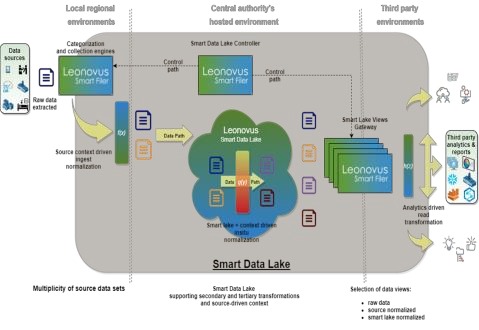
In addition to working with existing systems, the Leonovus solution aids in the digital transformation of the organization, by enabling state-of-the-art data concepts necessary for the data driven world. Data-driven business decisions and organizational actions based on analytical insights are rapidly becoming common practice. Data analytics and data science have evolved from spreadsheets through business intelligence (BI) cubes, to big data, streaming data, and comprehensive data sets for artificial intelligence (AI) and machine learning (ML). The use of collective data set repositories, such as data lakes and data warehouses, both on-premises and cloud-based, is
on the rise. The Leonovus data-centric security solution, includes these analytical architectures in its tool set. All of these capabilities are included in an automated solution requiring little operations effort and no new skills or expertise required.
The key to survival in the current and future cyber threat environment is to acknowledge there is no perfect way to keep intruders and bad actors out. With intrusion as an assumption, the highest priority is an IT infrastructure framework which has been designed from the start with a data-centric security model. To thrive, the data must survive!
1 MIT Technology Review Insights. (2015, July 20). Big Data, Big Security: Defense in Depth. Retrieved from MIT Technology Review: https://www.technologyreview.com/2015/07/20/167100/big-data-big-security-defense-in-depth/
